Cyber Threats:Types and Impect

The concept of “cyber threats” has become all too common in the current digital era. Cyber threats, which range from sophisticated phishing assaults to dangerous software, represent a genuine and expanding risk. However, what precisely are these dangers, and why should you give a damn? We’ll explore the realm of cyber risks, their effects, and—above all—how to safeguard your company and yourself in this piece.
Table of Contents
ToggleTypes of Cyber Threats

01:Malware
Malware, which stands for malicious software, is a general term for software intended to damage or take advantage of computer systems. It frequently enters your system undetected and can appear as worms, Trojan horses, or viruses.
02:Phishing Attacks
Phishing attacks are deviously written emails or messages that trick people into divulging sensitive information, like credit card numbers and passwords. They frequently pose as respectable companies or people.
03:DDoS Attacks
Attacks known as Distributed Denial of Service (DDoS) flood a network or website with too much traffic, making it unusable. Cybercriminals employ this technique to wreak havoc and interrupt services.
04:Ransomware
Malware that encrypts your data and holds it prisoner until you pay a ransom is known as ransomware. It has grown to be a significant worry for both people and companies.
05:Insider Threats
Insider threats are those who work for a company and abuse their access rights in order to compromise data. This could be deliberate or unintentional.
Impact of Cyber Threats
Cyber threats can have disastrous effects on their victims. To name a few, there could be reputational harm, financial losses, data breaches, and legal issues.
- Financial Losses:Financial losses are frequently caused by cyberattacks; these losses can include lost income, possible fines, and the expense of mitigating the attack.
- Data Breaches:Sensitive employee and consumer information may be revealed via data breaches, which may lead to monetary losses and legal repercussions.
- Reputational Damage:A cyber event can damage an organization’s reputation and undermine trust, which can have an impact on stakeholder confidence and customer loyalty.
- Legal and Regulatory Consequences:Adherence to data protection regulations is vital, as regulatory entities enforce stringent sanctions for breaches of data.
- Vulnerabilities and Attack Vectors:It is essential to comprehend the techniques and weaknesses that hackers take advantage of.
- Software Vulnerabilities:Cyber attacks frequently target systems that are unpatched and have outdated software.
- Social Engineering:Social engineering is a tactic used by cybercriminals to trick people into giving out private information. Be vigilant.
- Zero-Day Exploits:Zero-day exploits are difficult to protect against because they target software vulnerabilities that the program developer is unaware of.
- Supply Chain Attacks:Cybercriminals occasionally breach the hardware or software of a provider in order to access their target.
Cybersecurity Measures
- Firewalls and Intrusion Detection Systems:Putting in place firewalls and intrusion detection systems can assist in identifying possible threats and filtering out harmful information.
- Employee Training and Awareness:Cybersecurity best practices training for staff members helps stop social engineering scams.
- Encryption:Even in the unlikely event that unauthorized parties manage to access sensitive data, doing so can render it unintelligible.
- Incident Response Plans:To reduce harm in the case of a cyber attack, a clear incident response plan must be in place.
Social Engineering Attacks
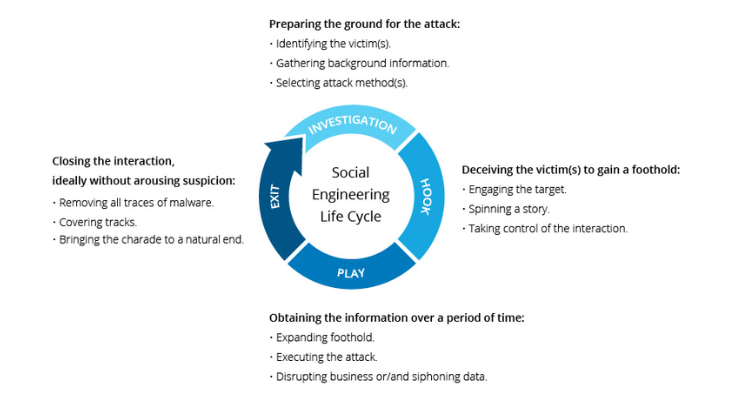
Social engineering is the practice of deceiving people into giving viruses a point of entry. Because the attacker impersonates a reputable actor, the victim unintentionally downloads malware on their device or divulges important information.
The following are some common forms of social engineering attacks:
- Baiting -Through a technique an assailant entices a victim of social engineering by offering an alluring reward, such as a complimentary gift card. The victim gives the attacker sensitive data, including login credentials.
- Pretexting is a tactic used by attackers to coerce their victim into divulging information under false pretenses, much to baiting. Usually, this entails pretending to be an official, like an IRS agent or a police officer, whose status will force the victim to comply.
- Phishing is when someone sends emails purporting to be from a reliable source. Phishing might be more focused, but it typically entails sending phony emails to as many users as possible. For instance, “whaling” targets high-value persons like CEOs, but “spear phishing” personalizes the email to target a single user.
- Voice phishing, or vishing, is when a con artist calls a victim and pretends to be the sender in order to obtain sensitive information or allow access to the victim’s system. Vishing can be used against anyone, but it usually targets the elderly.
- Smishing, often known as SMS phishing, is a tactic used by attackers to trick their target through text messages.
- Piggybacking is the practice of an authorized user giving someone else physical access so they can “piggyback” off the person’s login credentials. An employee might, for instance, give access to a someone pretending to be a new hire who misplaced their credential card.
- Tailgating is the practice of an unauthorized person entering a space after an authorized user has, say, swiftly entering through a locked door after the authorized user has opened it. This tactic is comparable to piggybacking, except the victim of tailgating is not aware that they are being exploited by someone else.
Supply Chain Attacks
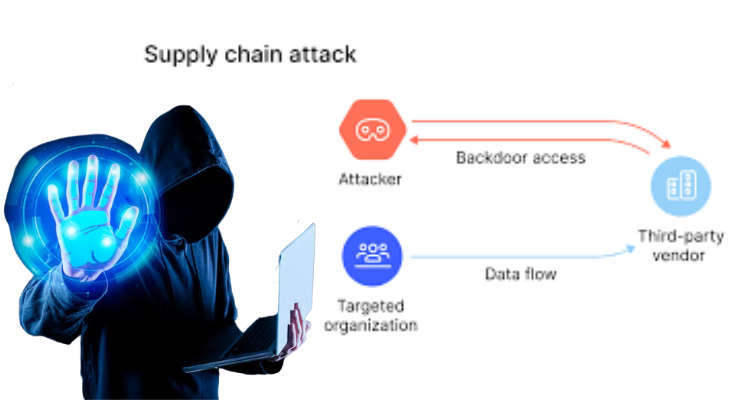
- Attacks on supply chains pose a fresh danger to vendors and software developers. Its goal is to spread malware using source code, build processes, or software update methods in order to infect and spread legal apps.
- In order to infiltrate the build and update processes, alter source code, and conceal harmful content, attackers search for vulnerabilities in server architecture, coding practices, and non-secure network protocols.
- Attacks on supply chains are particularly dangerous because the corrupted applications are signed and validated by reliable providers.The software vendor in a software supply chain attack is unaware that its updates or applications contain malware. The infected application’s trust and privileges are shared by malicious code.
Types of supply chain attacks include:
- Build tool or development pipeline compromise
- breach of developer credentials or code signing protocols
- malicious malware delivered to hardware or firmware components automatically
- Pre-installed malicious code on tangible devices
Man-in-the-Middle Attack
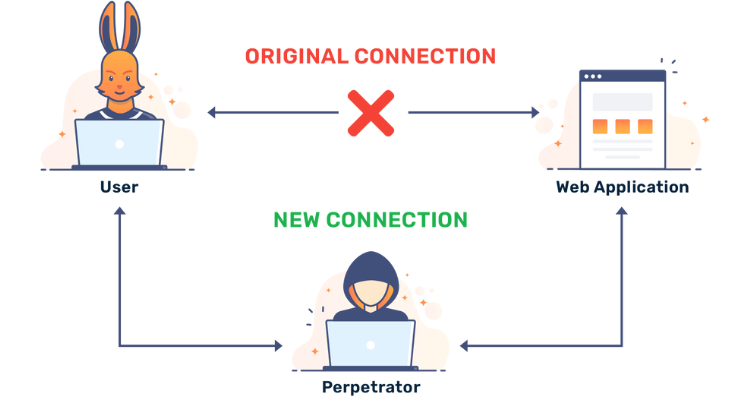
Intercepting the communication between two endpoints, like a user and an application, is known as a Man-in-the-Middle (MitM) attack. The attacker has the ability to impersonate each individual taking part in the conversation, eavesdrop on it, and take important data.
MitM attacks example:
- Wi-Fi eavesdropping is when a hacker creates a Wi-Fi network that people may connect to while impersonating a trustworthy party, such a company. The attacker may track connected users’ activities and intercept sensitive information like payment card numbers and login credentials thanks to the phony Wi-Fi.
- Email hijacking is when a hacker poses as a representative of a reputable company, like a bank, and utilizes that identity to deceive people into sending money or sensitive information to them. The user complies with what they believe to be bank instructions, but they are actually from the attacker.
- DNS spoofing when a Domain Name Server (DNS) is tricked, a malicious website masquerading as a trustworthy website is directed to the user. The hacker can take the user’s credentials or reroute traffic away from the trustworthy website.
- IP spoofing: a user’s IP address links them to a particular website. By pretending to be a website, an attacker can fool consumers into believing they are interacting with that website by spoofing an IP address.
- HTTPS spoofing is the practice of deceiving a browser into believing that a malicious website is secure, despite HTTPS being generally accepted as the more secure form of HTTP. The attacker hides the malicious nature of the website by using “HTTPS” in the URL.
Attack with Denial of Service
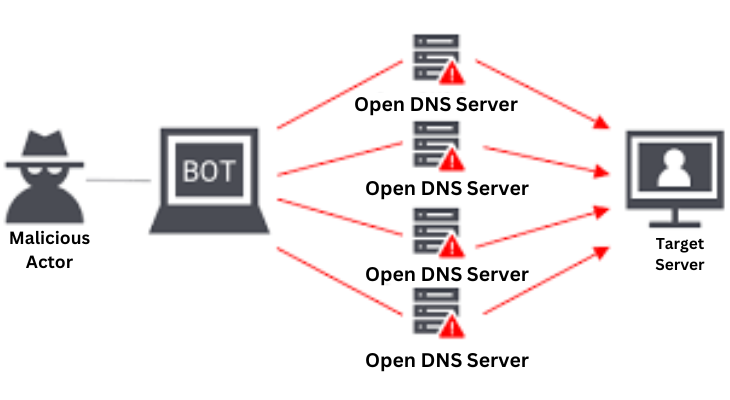
A Denial-of-Service (DoS) attack interferes with the target system’s ability to operate normally by flooding it with excessive traffic. A denial-of-service (DDoS) attack is an assault that takes advantage of several different devices.
Techniques for DoS attacks:
- HTTP flood DDoS: An attacker can overload a web server or application by sending out a large number of seemingly genuine HTTP requests. Generally, this strategy aims to push a target system to allocate as many resources as possible for each request; it does not require high bandwidth or packets that are faulty.
- SYN flood DDoS: Sending a SYN request, which the host must answer with a SYN-ACK acknowledging the request, and then the requester must reply with an ACK, is the first step in starting a Transmission Control Protocol (TCP) connection sequence. Attackers can take advantage of this sequence by issuing SYN requests and not listening for the host’s SYN-ACKs, which ties up server resources.
- DDoS via UDP flood: User Datagram Protocol (UDP) packets are broadcast to random ports, overwhelming a remote computer. By using up host resources, this approach compels the host to look for applications on the impacted ports and reply with “Destination Unreachable” packets.
- ICMP flood: An excessive amount of ICMP Echo Request packets overwhelm the destination and use up all available bandwidth, both inbound and outbound. The system slows down as a result of the servers’ inability to keep up with the volume of requests, even if they may attempt to reply to each one with an ICMP Echo Reply packet.
- NTP amplification: Because Network Time Protocol (NTP) servers are publicly accessible, an attacker can use this vulnerability to send a targeted server a lot of UDP traffic. The query-to-response ratio of 1:20 to 1:200, which enables an attacker to take advantage of open NTP servers to launch high-volume, high-bandwidth DDoS attacks, makes this attack an amplification.
Injection Attacks
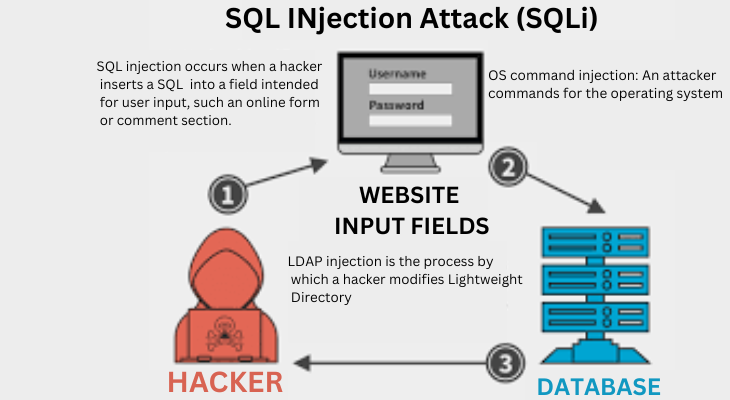
Injection attacks use a range of flaws to directly introduce malicious content into a web application’s code. Attacks that are successful could undermine the system as a whole, reveal private data, or launch a denial-of-service assault.
The following are a few of the most common injection attack vectors:
- SQL injection occurs when a hacker inserts a SQL query into a field intended for user input, such an online form or comment section. An application that is vulnerable will transmit the attacker’s data to the database and carry out any SQL commands that are inserted into the query. Because most web applications use databases built on Structured Query Language (SQL), SQL injection can occur. NoSQL attacks are a recent variation of this assault that targets databases devoid of relational data structures.
- Code injection: If an application is weak, an attacker may introduce code into it. The malicious code is carried out by the web server in the same way as if it were an application.
- OS command injection: An attacker can enter commands for the operating system to execute by taking advantage of a command injection vulnerability. This makes it possible for the assault to take over the system or exfiltrate OS data.
- LDAP injection is the process by which a hacker modifies Lightweight Directory Access Protocol (LDAP) searches by entering characters. If an unclean LDAP query is used by a system, it becomes susceptible. Because LDAP servers have the potential to store user identities and credentials for an entire business, these assaults are quite serious.
- XML eXternal Entities (XXE) Injection: This type of attack uses XML documents that have been specially created. Unlike previous attack vectors, this one takes advantage of unvalidated user inputs instead of inherent flaws in legacy XML parsers. It is possible to traverse pathways, run code remotely, and carry out server-side request forgery (SSRF) using XML documents.
- Cross-Site Scripting (XSS): In this attack, a malicious JavaScript string is entered by the attacker. The code is executed by the target’s browser, giving the attacker the ability to take over a user’s session or reroute them to a malicious website by stealing session cookies. If an application does not sanitize user inputs to remove JavaScript code, it is susceptible to cross-site scripting (XSS).
Conclusion
To sum up, identifying and thwarting cyberattacks is a continuous effort. By adhering to recommended procedures, remaining knowledgeable, and putting strong security measures in place, you may greatly lower the risks related to cyberattacks. Remain alert and keep in mind that both individuals and companies must work together to defend against cyber attacks.
FAQs
What are common signs of a cyber threat?
Unexpected system slowdowns, odd network activity, and unwanted email attachments are warning signs.
How can individuals protect themselves from cyber threats?
People should enable two-factor authentication, use strong, one-of-a-kind passwords, and update their software and hardware frequently.
What should businesses do in the event of a data breach?
Companies should have an incident response plan in place that covers, among other things, alerting relevant authorities and parties affected as needed.
How can I keep up with the latest developments in cyber threats?
Keeping up with security changes, taking part in training, and keeping an eye on cybersecurity news sources are all part of staying informed.




One Comment